Instructions relating to performaing a GDPR DPIA
- What are the key elements of a DPIA process?
- Is there a template we can use?
- Who is responsible for the DPIA?
- Who should be involved in the DPIA?
- What is the role of the DPO?
- Step 1: How do we decide whether to do a DPIA?
- Step 2: How do we describe the processing?
- Step 3a: Do we need to consult individuals?
- Step 3b: Do we need to consult anyone else?
- Step 4: How do we assess necessity and proportionality?
- Step 5: How do we identify and assess risks?
- Step 6: How do we identifying mitigating measures?
- Step 7: How do we conclude our DPIA?
- What happens next?
Instructions to perform a Data Protection Impact Assessment
What are the key elements of a DPIA process?
A DPIA should begin early in the life of a project, before you start your processing, and run alongside the planning and development process. It should include these steps:
Step 1: identify the need for a DPIA
Step 2: describe the processing
Step 3: consider consultation
Step 4: assess necessity and proportionality
Step 5: identify and assess risks
Step 6: identify measures to mitigate the risks
Step 7: sign off and record outcomes
After sign-off you should integrate the outcomes from your DPIA back into your project plan, and keep your DPIA under review. Throughout this process, you should consult individuals and other stakeholders as needed.
The DPIA process is designed to be flexible and scalable. You can design a process that fits with your existing approach to managing risks and projects, as long as it contains these key elements.
You can also scale the time and resources needed for a DPIA to fit the nature of the project. It does not need to be a time-consuming process in every case.
Is There A Template We Can Use?
You can make your own to suit your needs, or use an existing project-management method, as long as it covers all the key elements of the process. If you are making your own template, you may find it helpful to refer to the Criteria for an acceptable DPIA in Annex 2 of the Article 29 working party guidelines.
Who is responsible for the DPIA?
You can decide who has responsibility for carrying out DPIAs in your organisation, and who signs them off. You can outsource your DPIA, but you remain responsible for it. If you have a Data Protection Officer (DPO), you must ask for their advice on your DPIA, and document it as part of the process.You may want to ask a processor to carry out a DPIA on your behalf if they do the relevant processing operation, but again you remain responsible for it.
Who should be involved in the DPIA?
As well as the business area or individual who is leading on the project or process requiring the DPIA, you should also involve:* a DPO, if you have one;
* information security staff;
* any processors; and
* legal advisors or other experts, where relevant.
What is the role of the DPO?
If you have a DPO, you must seek their advice. The DPO should provide advice on:* whether you need to do a DPIA;
* how you should do a DPIA;
* whether to outsource the DPIA or do it in-house;
* what measures and safeguards you can take to mitigate risks;
* whether you’ve done the DPIA correctly; and
* the outcome of the DPIA and whether the processing can go ahead.
* You should record your DPO’s advice on the DPIA. If you don’t follow their advice, you should record your reasons and ensure you can justify your decision.
DPOs must also monitor the DPIA’s ongoing performance, including how well you have implemented your planned actions to address the risks.
Under Article 39 of GDPR, DPOs have specific tasks regarding DPIAs. This is why you must ensure that any responsibilities you give a DPO for your DPIA do not conflict with their ability to complete these tasks in an independent manner, as required by Recital 97.
Step 1: How do we decide whether to do a DPIA?
Ask your DPO for advice. If you have any major project that involves the use of personal data, it is good practice to do a DPIA. If you already intend to do a DPIA, go straight to step 2.Otherwise, you need to check whether your processing is on the list of types of processing that automatically require a DPIA. If not, you need to screen for other factors that may indicate it is a type of processing that is likely to result in high risk, such as processing the data of vulnerable individuals.
You can use or adapt the checklists at the end of this guidance to help you do this screening. You can also read ‘When do we need to do a DPIA?’ for more guidance.
If you do this screening and decide a DPIA is not needed, you should document your decision and the reasons for it, including your DPO’s advice. This does not have to be a burdensome paperwork exercise. It just needs to help you demonstrate you have properly considered and complied with your DPIA obligations. For example, you could simply keep an annotated copy of the checklist.
If you are in any doubt, we strongly recommend you do a DPIA.
Step 2: How do we describe the processing?
Describe how and why you plan to use the personal data. Your description must include “the nature, scope, context and purposes of the processing”. The nature of the processing is what you plan to do with the personal data. This should include, for example:* how you collect the data;
* how you store the data;
* how you use the data;
* who has access to the data;
* who you share the data with;
* whether you use any processors;
* retention periods;
* security measures;
* whether you are using any new technologies;
* whether you are using any novel types of processing; and
* which screening criteria you flagged as likely high risk.
The scope of the processing is what the processing covers. This should include, for example:
* the nature of the personal data;
* the volume and variety of the personal data;
* the sensitivity of the personal data;
* the extent and frequency of the processing;
* the duration of the processing;
* the number of data subjects involved; and
* the geographical area covered.
The context of the processing is the wider picture, including internal and external factors which might affect expectations or impact. This might include, for example:
* the source of the data;
* the nature of your relationship with the individuals;
* how far individuals have control over their data;
* how far individuals are likely to expect the processing;
* whether these individuals include children or other vulnerable people;
* any previous experience of this type of processing;
* any relevant advances in technology or security;
* any current issues of public concern; * in due course, whether you comply with any GDPR codes of conduct (once any have been approved under Article 40) or GDPR certification schemes;and
* whether you have considered and complied with relevant codes of practice.
The purpose of the processing is the reason why you want to process the personal data. This should include:
* your legitimate interests, where relevant;
* the intended outcome for individuals; and
* the expected benefits for you or for society as a whole.
Step 3a: Do we need to consult individuals?
You should seek and document the views of individuals (or their representatives) unless there is a good reason not to do it.In most cases it should be possible to consult individuals in some form. However, if you decide this is not appropriate, you should record this decision as part of your DPIA, with a clear explanation. For example, you may be able to demonstrate that consultation would compromise commercial confidentiality, undermine security, or be disproportionate or impracticable.
If the DPIA covers the processing of personal data of existing contacts (for example, existing customers or employees), you should design a consultation process to seek the views of those particular individuals, or their representatives.
If the DPIA covers a plan to collect the personal data of individuals you have not yet identified, you may need to carry out a more general public- consultation process, or targeted research. This could take the form of market research with a certain demographic or contacting relevant campaign or consumer groups for their views.
If your DPIA decision differs from the views of individuals, you need to document your reasons for disregarding their views.
Step 3b: Do we need to consult anyone else?
If you use a data processor, you may need to ask them for information and assistance. Your contracts with processors should require them to assist.You should consult all relevant internal stakeholders, in particular anyone with responsibility for information security.
We also recommend you consider seeking legal advice or advice from other independent experts such as IT experts, sociologists or ethicists where appropriate. However, there are no specific requirements to do so.
Step 4: How do we assess necessity and proportionality?
You should consider: Do your plans help to achieve your purpose?Is there any other reasonable way to achieve the same result?
The Article 29 guidelines also say you should include how you ensure data protection compliance, which are a good measure of necessity and proportionality. In particular, you should include relevant details of:
* your lawful basis for the processing;
* how you will prevent function creep;
* how you intend to ensure data quality;
* how you intend to ensure data minimisation;
* how you intend to provide privacy information to individuals;
* how you implement and support individuals' rights;
* measures to ensure your processors comply; and
* safeguards for international transfers.
Step 5: How do we identify and assess risks?
Consider the potential impact on individuals and any harm or damage your processing may cause – whether physical, emotional or material. In particular, look at whether the processing could contribute to:* inability to exercise rights (including but not limited to privacy rights);
* inability to access services or opportunities;
* loss of control over the use of personal data;
* discrimination;
* identity theft or fraud;
* financial loss;
* reputational damage;
* physical harm;
* loss of confidentiality;
* re-identification of pseudonymised data; or
* any other significant economic or social disadvantage
You should include an assessment of the security risks, including sources of risk and the potential impact of each type of breach (including illegitimate access to, modification of or loss of personal data).
To assess whether the risk is a high risk, you need to consider both the likelihood and severity of the possible harm. Harm does not have to be inevitable to qualify as a risk or a high risk. It must be more than remote, but any significant possibility of very serious harm may still be enough to qualify as a high risk. Equally, a high probability of widespread but more minor harm may still count as high risk.
You must make an objective assessment of the risks. It is helpful to use a structured matrix to think about likelihood and severity of risks:
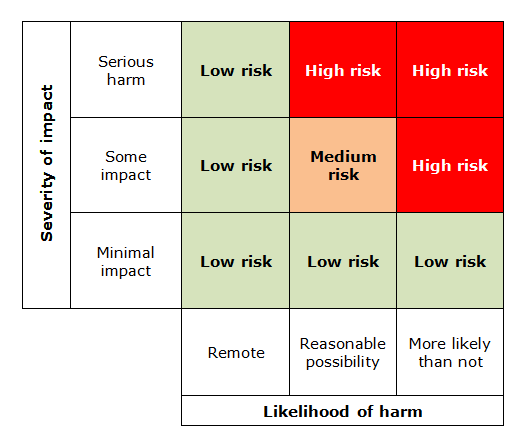
The above matrix shows a structured way to assess risk. Your organisation may use a different method you can adapt for the same purpose.
You may also want to consider your own corporate risks, such as the impact of regulatory action, reputational damage or loss of public trust.
Step 6: How do we identify mitigating measures?
Against each risk identified, record its source. You should then consider options for reducing that risk. For example:* deciding not to collect certain types of data;
* reducing the scope of the processing;
* reducing retention periods;
* taking additional technological security measures;
* training staff to ensure risks are anticipated and managed;
* anonymising or pseudonymising data where possible;
* writing internal guidance or processes to avoid risks;
* using a different technology;
* putting clear data-sharing agreements into place;
* making changes to privacy notices;
* offering individuals the chance to opt out where appropriate; or
* implementing new systems to help individuals to exercise their rights.
This is not an exhaustive list, and you may be able to devise other ways to help reduce or avoid the risks. You should ask your DPO for advice.
Record whether the measure would reduce or eliminate the risk. You can take into account the costs and benefits of each measure when deciding whether or not they are appropriate.
Step 7: How do we conclude our DPIA?
You should then record:* what additional measures you plan to take;
* whether each risk has been eliminated, reduced, or accepted;
* the overall level of ‘residual risk’ after taking additional measures; and
* whether you need to consult the ICO.
You do not always have to eliminate every risk. You may decide that some risks, and even a high risk, are acceptable given the benefits of the processing and the difficulties of mitigation. However, if there is still a high risk, you need to consult the ICO before you can go ahead with the processing.
As part of the sign-off process, you should seek and document DPO advice on whether the processing is compliant and can go ahead. If you decide not to follow their advice, you need to record your reasons.
You should also record any reasons for going against the views of individuals or other consultees.
What happens next?
You must integrate the outcomes of your DPIA into your project plans. You should identify any action points and who is responsible for implementing them. You can use the usual project-management process to ensure these are followed through.You should monitor the ongoing performance of the DPIA. You may need to cycle through the process again before your plans are finalised.
If you have decided to accept a high risk, either because it is not possible to mitigate or because the costs of mitigation are too high, you must consult the ICO before you go ahead with the processing. See the next section for more information on this consultation process.
To aid transparency and accountability, it is good practice to publish your DPIA. This could help foster trust in your processing activities, and improve individuals’ ability to exercise their rights. If you are concerned that publication may reveal commercially sensitive information, undermine security or cause other risks, you should consider whether you can redact (black out) or remove sensitive details, or publish a summary.
When considering publishing DPIAs, public authorities should think about their wider transparency obligations, such as complying with the Freedom of Information Act. Before GDPR, many public authorities included privacy impact assessments in their definition documents for publication schemes.
You need to keep your DPIA under review. You may need to repeat it if there is a substantial change to the nature, scope, context or purposes of your processing.
